Teleport Expands Secure Identity Platform for Growth

Secure infrastructure company Teleport today outlined a wide-ranging vision and new products for infrastructure identity, an innovative approach to securing infrastructure across clouds and datacenters.
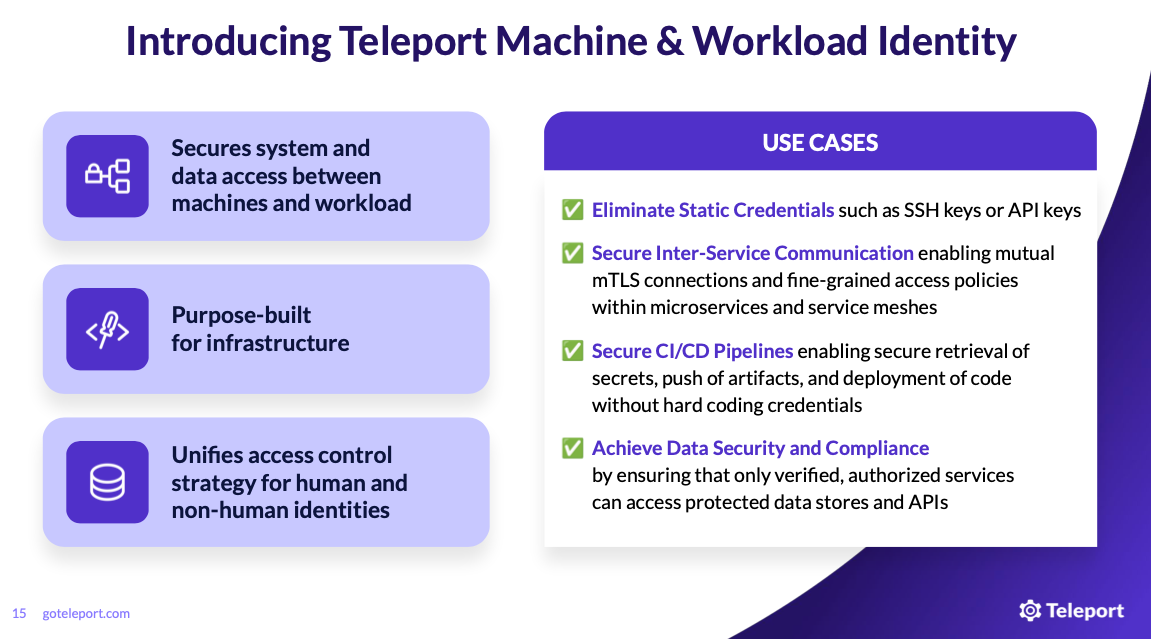
As part of its platform upgrade, Teleport has introduced the concept of Infrastructure Identity as well as a new product, Teleport Machine & Workload Identity. The new architecture and product help enforce zero-trust security models by verifying every entity in the infrastructure—human or machine—before granting access. Teleport says this will help organizations secure inter-service communication, eliminate static credentials in CI/CD pipelines, and achieve compliance mandates with audit features.
Making All Compute Trustworthy
Teleport has an ambitious goal to change how access to critical infrastructure is managed. The company is focused on eliminating anonymous computing by permitting human or machine access only when there is a task that needs to be performed. It also provides granular tracking activity in critical business systems.
The company's Infrastructure Identity approach differs from niche solutions such as virtual private networks (VPNs) and identity access management (IAM) solutions that require specific credentials or cryptographic keys. One of the big goals of Teleport’s Infrastructure Identity approach is to eliminate all static access credentials, instead using cryptographic identity based on real-world attributes. This approach takes aim at the fragmented nature of current identity and access solutions, which are often implemented either in piecemeal fashion or with expensive DIY integrations.
Ev Kontsevoy, CEO and co-founder at Teleport, told me in a recent interview that the opportunity is huge because most companies have built their own identity and security solutions, which are expensive and complicated to manage:
"Currently, most identity and security solutions are oriented towards IT use cases and are fragmented and siloed for different technologies. Recently, we have seen security emerge as a core function in engineering and in platform engineering teams, in order to address the complexity, scale, and automation in these environments. For these teams, we modernize infrastructure access, identity and policy, giving them a unified, vertically integrated architecture. This unified identity approach gets rid of anonymous computing, enabling our customers to keep track of and govern everyone and everything that is happening in their infrastructure in one place. And these identities are based on real world attributes that can't be stolen, lost or shared.”
With this approach, Teleport says it can support a wide range of cloud infrastructure devices and development environments. These include servers (Windows and Linux), Windows RDP, SSH, Kubernetes clusters, databases, DevOps tools (such as the AWS Management Console), CI/CD, GitHub, and various monitoring dashboards. It also supports Web applications.
Inside the Teleport Machine
The Teleport Machine & Workload Identity solution aims to make secure access pervasive and easier, which is key for cloud engineers who must often grant access to assets and resources on the fly to enable faster development.
The challenges of secure access are growing as cloud environments become more distributed and wide-reaching with the implementation of Kubernetes, hybrid cloud, and containers. Teleport says that the number of identities for specific compute assets now exceeds that of humans, so traditional security models, which often require the management of complex databases of credentials and secrets, can no longer support this scale.
Teleport Machine & Workload identity targets the security of compute assets by ensuring that access to every asset is trusted, authorized, and audited. Key capabilities of the Teleport Machine & Workload Identity release include:
-
Service Discovery – Inventories machine and workload identities across diverse environments.
-
Secretless Authentication – Replaces API keys and long-term secrets with short-lived X.509 certificates, eliminating the risks of overprivileged, anonymous accounts.
-
Ephemeral Authorization – Supports fine-grained Attribute-Based and Role-Based Access Control (ABAC/RBAC) for workload interactions, ensuring the right workloads access only to what they need.
-
Auditability & Compliance – Provides detailed logging and exportable audit trails for compliance frameworks such as HIPAA, GDPR, SOC 2, and FedRAMP.
-
Seamless Integration – Works with open-source policy agents, developer APIs, JWT and SPIFFE standards, and bootstrapping trust, enabling interoperability across infrastructure.
Embracing a Platform Growth Approach
Teleport, which was recently named to our Futuriom 50 list of the most promising private companies in cloud and communications infrastructure, says its has recently logged sales growth of approximately 50% per year. The company has traction at large organizations, including three of the top five financial services companies and five of the top 20 market-capitalization companies in the world. Customers include Nasdaq, Databricks, DoorDash, Elastic, GitLab, Snowflake, and Vonage, among others.
As mentioned by Kontsevoy, the company’s approach also embraces the platform engineering movement, in which organizations look to implement technology with high-level strategy and compliance rather than implementing technology piecemeal through individual departments. Infrastructure security is a growing part of platform engineering, as most organizations do not want a fragmented approach to security—they'd like to see a consistent, pervasive approach to infrastructure security throughout the organization, which is what Teleport is proposing.
Futuriom Take: Teleport is uniquely positioned to take advantage of key trends in the cloud infrastructure industry: the lack of easy-to-manage identity access solutions as well as the need for centralized security management and compliance through platform engineering.